Unlocking the Power of OAuth Governance for Managed Service Providers
- Mandi @ MSPwerks

- Oct 23, 2025
- 4 min read
Updated: Dec 22, 2025
OAuth Governance as a Managed Service helps MSPs turn app permissions, webhook monitoring, and evidence reporting into recurring revenue. It extends your managed security stack beyond MFA and patching—giving clients continuous visibility into which apps and integrations can access their data, and proof that those access rights are reviewed.
Why OAuth Governance Is the Next Layer in Managed Security
Every connected business tool—CRM, HR, automation—relies on OAuth permissions and webhooks. You’ve already protected endpoints and enforced MFA, but OAuth remains a blind spot.
Unverified publishers, expiring secrets, and shadow integrations expose data silently. Auditors now ask who approved which apps and how often those approvals are reviewed. OAuth governance answers both—and creates a billable service opportunity.

What It Means for MSPs
Most MSPs start manually—exporting data with PowerShell, tracking in spreadsheets, and emailing evidence. That might work once a year but doesn’t scale.
With AppGuard360, OAuth governance becomes continuous and automated, including discovery, risk scoring, expiration alerts, and branded evidence packs across all tenants.

Common Client Pain Points Create Opportunities
Understanding client pain points is crucial. Many clients struggle with managing app permissions and ensuring compliance. This presents an opportunity for MSPs to step in and provide a solution that not only addresses these issues but also adds value to their service offerings.
The Importance of Continuous Monitoring
Continuous monitoring is essential in today’s fast-paced digital environment. Clients need to know that their data is secure at all times. By implementing OAuth governance, MSPs can provide peace of mind, knowing that they are actively managing and monitoring app permissions.
Building Trust Through Transparency
Transparency is key in building trust with clients. By offering clear insights into app permissions and integrations, MSPs can demonstrate their commitment to security and compliance. This transparency fosters stronger relationships and encourages long-term partnerships.
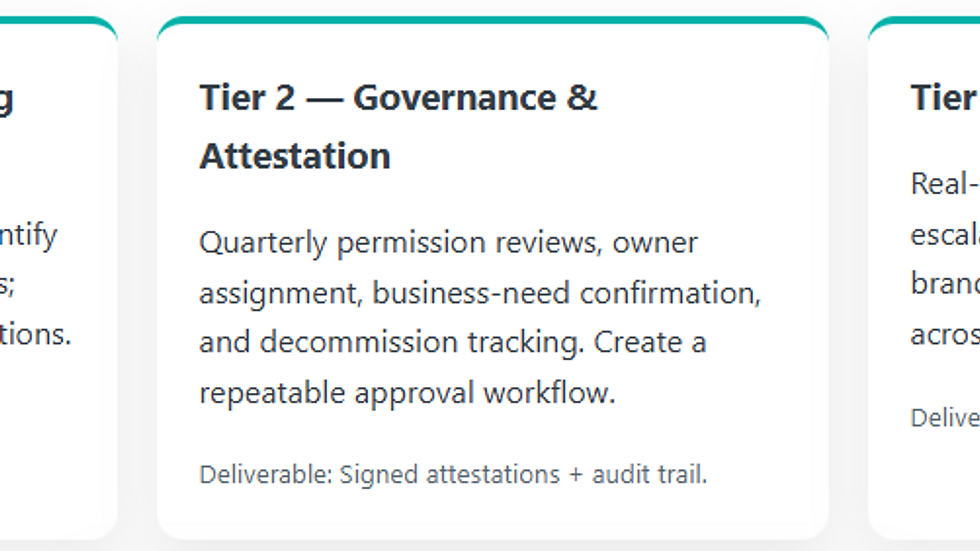
How to Package the Service
MSPs can transform OAuth governance from a one-time audit into a recurring managed service. By packaging capabilities into three tiers of visibility, governance, and continuous monitoring, providers deliver consistent results, simplified compliance, and tangible client trust.
Mapping to Compliance Outcomes
OAuth governance supports compliance and cyber-insurance by controlling app permissions and monitoring access to sensitive data. It aligns with frameworks like SOC 2 (CC6.6) and ISO 27001 (A.9), ensuring least-privilege access and maintaining audit trails for GDPR, HIPAA, and similar mandates.
A strong OAuth governance strategy also reinforces cyber-insurance readiness — providing evidence of access control, breach prevention, and policy enforcement. By identifying risky integrations and verifying user permissions, MSPs help clients prove security maturity and improve coverage terms.
In short, OAuth governance bridges compliance, insurance, and risk management — delivering measurable proof that access is secure, reviewed, and auditable.
Framework | Control Example |
SOC 2 (CC6.6) | Logical access oversight & periodic access review |
ISO 27001 (A.9) | Authorization management & least-privilege control |
Cyber Insurance | Evidence of app governance & third-party access review |

Proving Value to Clients
Go beyond uptime and patch reports. Executive-friendly visuals show progress clients understand:

Verified vs Unverified Apps
Show which connected apps are verified publishers and which are not — giving leadership clear visibility into trusted integrations versus unapproved or risky third-party tools. This helps MSPs demonstrate governance maturity and proactive oversight.
Pending Ownership Reviews
Highlight apps or service principals awaiting business owner approval or attestation. This not only simplifies quarterly reviews but also proves that your MSP maintains accountability for every integration’s purpose and owner.
Secret Expirations and Resolution
Visualize upcoming token or certificate expirations and their resolution status. Clients see your MSP acting ahead of outages and compliance issues — reinforcing your value as a proactive partner, not just a support provider.
Each QBR now demonstrates measurable security improvement — with visuals that make governance tangible and audit-ready.

Pricing and Positioning
Offer OAuth Governance as a recurring managed service, not a one-time audit. The goal is to create predictable monthly revenue while delivering measurable client assurance. Each pricing model should align with how your MSP packages other security and compliance services.
Per-Tenant Model:
Charge a small monthly fee per client environment for continuous OAuth monitoring, evidence generation, and risk scoring. Ideal for smaller MSPs or co-managed clients who prefer à la carte pricing.
Add-On Model:
Bundle OAuth Governance into your Microsoft 365 security or compliance plans. This increases average deal size and helps differentiate your MSP from those who only offer MFA and endpoint protection.
Fixed Monthly Model:
Include OAuth Governance within your advanced security or compliance tiers, providing unlimited coverage as part of a flat-rate subscription. This model simplifies renewals and locks in long-term client retention.
Pricing should emphasize assurance and outcomes, not tooling. Clients aren’t paying for scripts or dashboards — they’re investing in evidence-backed trust that proves your MSP is managing access, governance, and compliance continuously.
Objection Handling
Addressing Common Concerns
When introducing OAuth governance, clients may have concerns. They might wonder about the complexity of implementation or the value it adds. Be prepared to address these objections with clear, concise explanations.
Providing Evidence of Value
Use case studies or testimonials to illustrate the benefits of OAuth governance. Show potential clients how other businesses have successfully implemented this service and the positive outcomes they experienced.
Ready to Add OAuth Governance to Your Stack?
Forward-thinking MSPs are packaging OAuth oversight as a service their clients trust. Start with the Blueprint, then scale with AppGuard360 to automate discovery, monitoring, and evidence across tenants.




